
Published on October 28, 2025
Mitigating Third-Party Risks: Enhancing Security Protocols for Vendor and Supply Chain Management
Mitigating Third-Party Risks: Enhancing Security Protocols for Vendor and Supply...
Read more...
789 Views
Published on October 27, 2025
Post-Quantum Cryptography: Developing Encryption Methods for Future-Proof Cybersecurity
Post-Quantum Cryptography: Developing Encryption Methods for Future-Proof Cybers...
Read more...
847 Views
Published on October 24, 2025
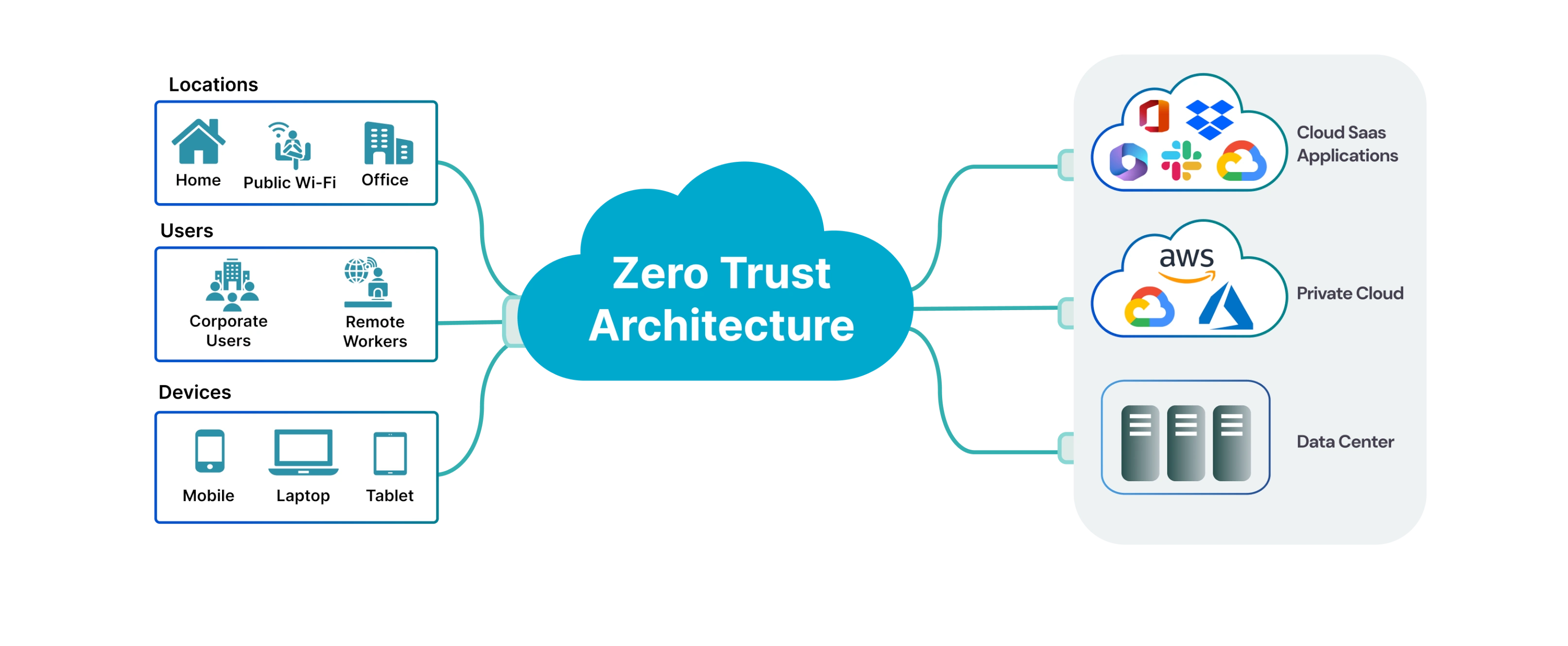
Implementing Zero-Trust Architecture: Strengthening Network Security with Continuous Authentication
Implementing Zero-Trust Architecture: Strengthening Network Security with Contin...
Read more...
830 Views

Published on October 22, 2025
AI-Driven Cyber Attacks: Emerging Threats and Countermeasures in Modern Security Infrastructure
AI-Driven Cyber Attacks: Emerging Threats and Countermeasures in Modern Security...
Read more...
849 Views

