
Published on October 28, 2025
Mitigating Third-Party Risks: Enhancing Security Protocols for Vendor and Supply Chain Management
Mitigating Third-Party Risks: Enhancing Security Protocols for Vendor and Supply...
Read more...
600 Views
Published on October 27, 2025
Post-Quantum Cryptography: Developing Encryption Methods for Future-Proof Cybersecurity
Post-Quantum Cryptography: Developing Encryption Methods for Future-Proof Cybers...
Read more...
645 Views

Published on October 23, 2025
Building Operational Resilience: Ensuring Business Continuity Post-Cybersecurity Breach
Building Operational Resilience: Ensuring Business Continuity Post-Cybersecurity...
Read more...
679 Views
Published on October 08, 2025
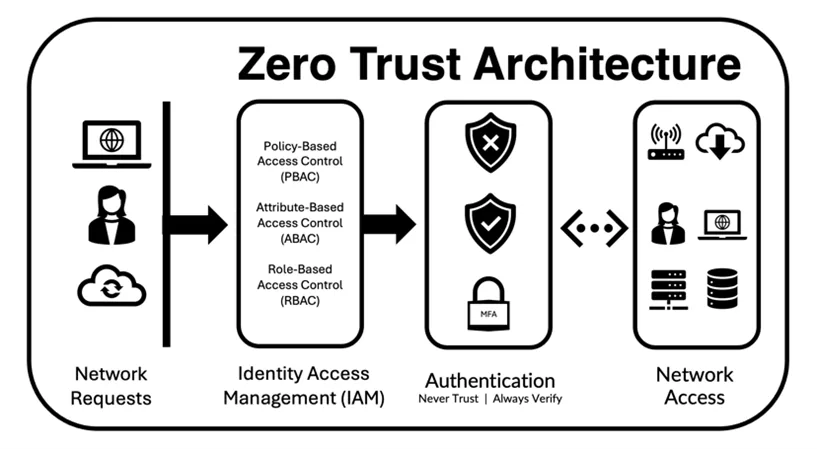
Securing Web Applications with Zero Trust Architecture: A Modern Approach
Securing Web Applications with Zero Trust Architecture: A Modern ApproachHave yo...
Read more...
793 Views

Published on May 13, 2025
How to Run Dependency Audits with GitHub Copilot
How to Run Dependency Audits with GitHub CopilotHave you pondered how many secur...
Read more...
701 Views

Published on April 08, 2025
Building an AI-powered Cybersecurity Assistant with DeepSeek
Every developer understands that even well-intentioned applications may be insec...
Read more...
621 Views

