October 08, 2025
Securing Web Applications with Zero Trust Architecture: A Modern Approach
Securing Web Applications with Zero Trust Architecture: A Modern Approach
Have you wondered if your web-based apps are secure? It is easy to believe that everything within is safe when the network perimeter is strong. But this old way of doing things is not enough anymore. Zero Trust Architecture or ZTA is a new method of maintaining your network security that does not trust anyone by default. This article will talk about Zero Trust, why it is necessary for web app security, and how to implement it. Ready for this game-changing approach? Let's begin!
What is Zero Trust Architecture?
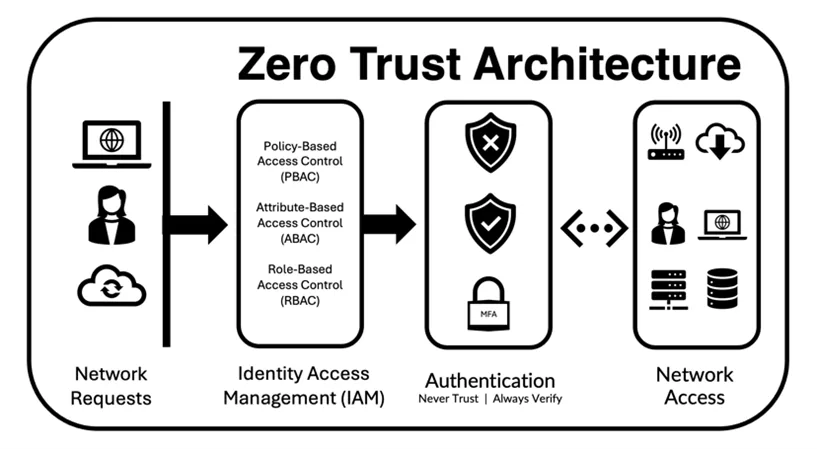
Zero Trust Architecture (ZTA) follows 'never trust, always verify' security. Zero Trust considers attacks within and outside the network, unlike perimeter-based security. This means everyone, gadget, and program is untrustworthy until proven differently.
ZTA applies strict identity verification and ongoing access monitoring to limit resource access to approved users and devices. Even if an attacker gains access to one area of the network, the goal is to limit lateral movement. With remote work and cloud computing, data breaches and insider threats have increased. This strategy protects against them.
Zero Trust continuously checks and verifies every access request, not just at the network perimeter.
Key Principles of Zero Trust
Zero Trust has several essential concepts that ensure only authorised individuals and devices can access critical data or systems. Take a look at these:
Verify Every User and Device
Authenticate and authorise all users and devices in a Zero Trust model, regardless of their location within or outside the corporate network. This usually involves MFA and device compliance checks. You can use Auth0 or Okta to implement MFA in code. Example of Node.js authentication using Passport.js:
const passport = require('passport');
const LocalStrategy = require('passport-local').Strategy;
passport.use(new LocalStrategy((username, password, done) => {
// Validate user credentials here
User.findOne({ username: username }, (err, user) => {
if (err) return done(err);
if (!user) return done(null, false);
if (user.password !== password) return done(null, false);
return done(null, user);
});
}));
Least Privilege Access
Everyone and everything has the access they need to do their jobs. This makes the system less vulnerable to damage and loss if someone breaks in. Role-based access control (RBAC) is a way to limit who can see what data.
const roles = {
user: ['read'],
admin: ['read', 'write', 'delete'],
};
function checkAccess(userRole, resource) {
if (roles[userRole].includes(resource)) {
return true;
}
return false;
}
Micro-Segmentation
Zero Trust divides the network into discrete components. This restricts attackers' network movement and helps contain intrusions. API Gateways and Firewalls can micro-segment your application to restrict access.
Continuous Monitoring and Validation
Zero Trust validates access requests throughout the session rather than just after authentication. This covers user behaviour monitoring and access privileges maintenance. Node.js can continually validate requests using JWT tokens.
const jwt = require('jsonwebtoken');
function authenticateToken(req, res, next) {
const token = req.header('Authorization');
if (!token) return res.status(403).send('Access Denied');
jwt.verify(token, process.env.TOKEN_SECRET, (err, user) => {
if (err) return res.status(403).send('Invalid token');
req.user = user;
next();
});
}Zero Trust strengthens online application security by following these principles, minimising the risk of unauthorised access and minimising breaches.
Implementing Zero Trust for Web Applications
Zero Trust for web apps is hard to set up but works well to protect app resources. Do these things to start making a Zero Trust way for your web apps:
Step 1: Identity and Access Management (IAM)
Identity and Access Management must work well for Zero Trust to work. Use multi-factor authentication to prove who all web app users and gadgets are. Okta or Azure AD could login users. How to use Passport.js for Node.js backend user authentication:
const passport = require('passport');
const LocalStrategy = require('passport-local').Strategy;
passport.use(new LocalStrategy(
function(username, password, done) {
User.findOne({ username: username }, function (err, user) {
if (err) { return done(err); }
if (!user) { return done(null, false); }
if (user.password !== password) { return done(null, false); }
return done(null, user);
});
}
));
Step 2: Micro-Segmentation and Policy Enforcement
Segment your application into layers instead of relying the internal network. It is not suggested to put your database layer on the same network segment as your web servers. This will result in reducing the chance of application side movement. However, you can enforce security policies at all entry points through API gateways such as Kong.
Step 3: Continuous Monitoring and Adaptive Access Control
Splunk or Datadog can keep track of user and device activity in real time. These methods track suspicious activity and employ adaptive access control to adjust access rights based on user behaviour, location, and device security.
See how JWT tokens can maintain validation:
const jwt = require('jsonwebtoken');
function authenticateToken(req, res, next) {
const token = req.header('Authorization');
if (!token) return res.status(403).send('Access Denied');
jwt.verify(token, process.env.TOKEN_SECRET, (err, user) => {
if (err) return res.status(403).send('Invalid token');
req.user = user;
next();
});
}
Conclusion
Web application security is heading towards Zero Trust Architecture in the current threat environment. Distrusting by default, zero trust is a better security model than traditional ways. Continuous authentication, least privilege access, and robust identity management protect web applications against different threats. The principles and technology of this article will assist you in creating secure, robust web applications that are capable of resisting contemporary cyber attacks.
950 views
